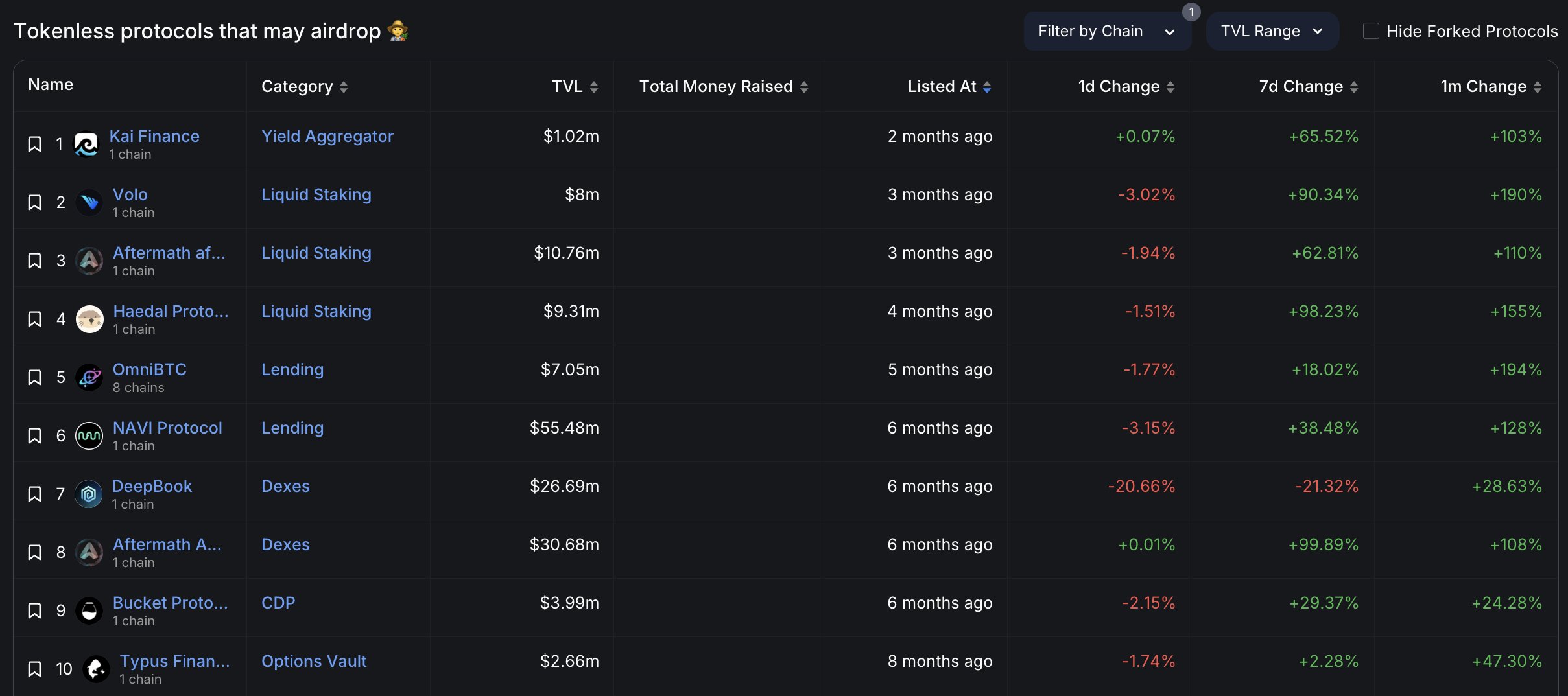
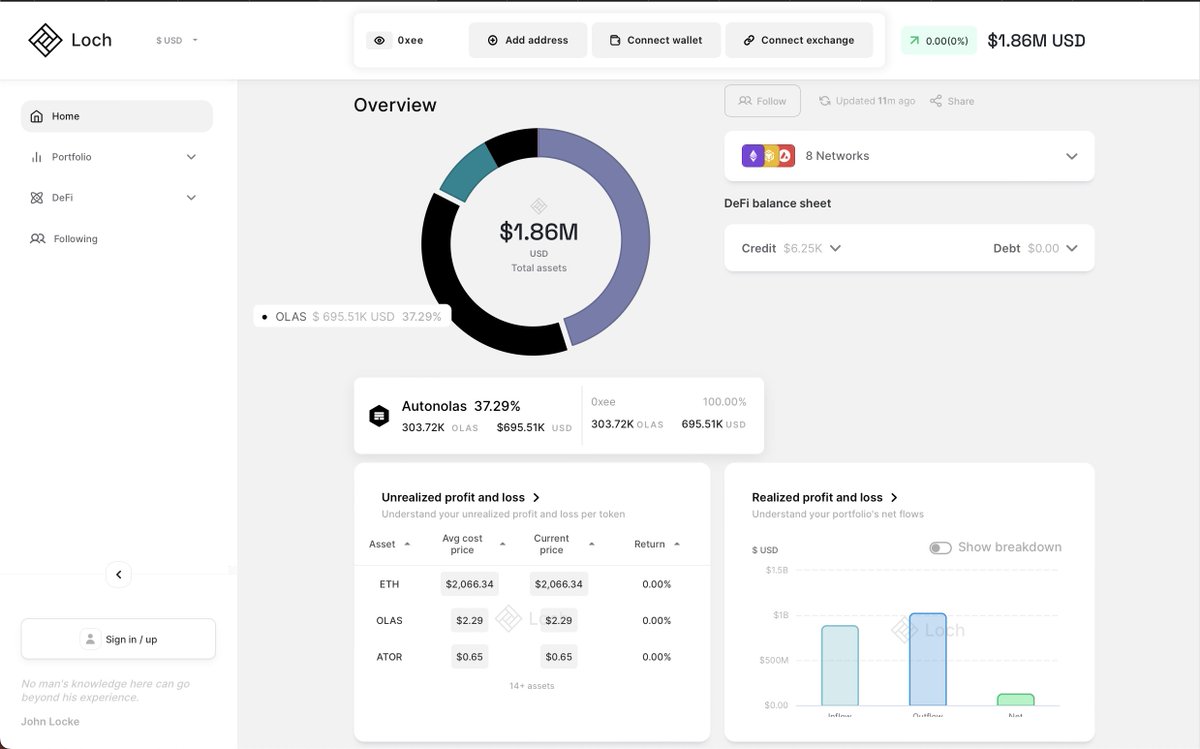
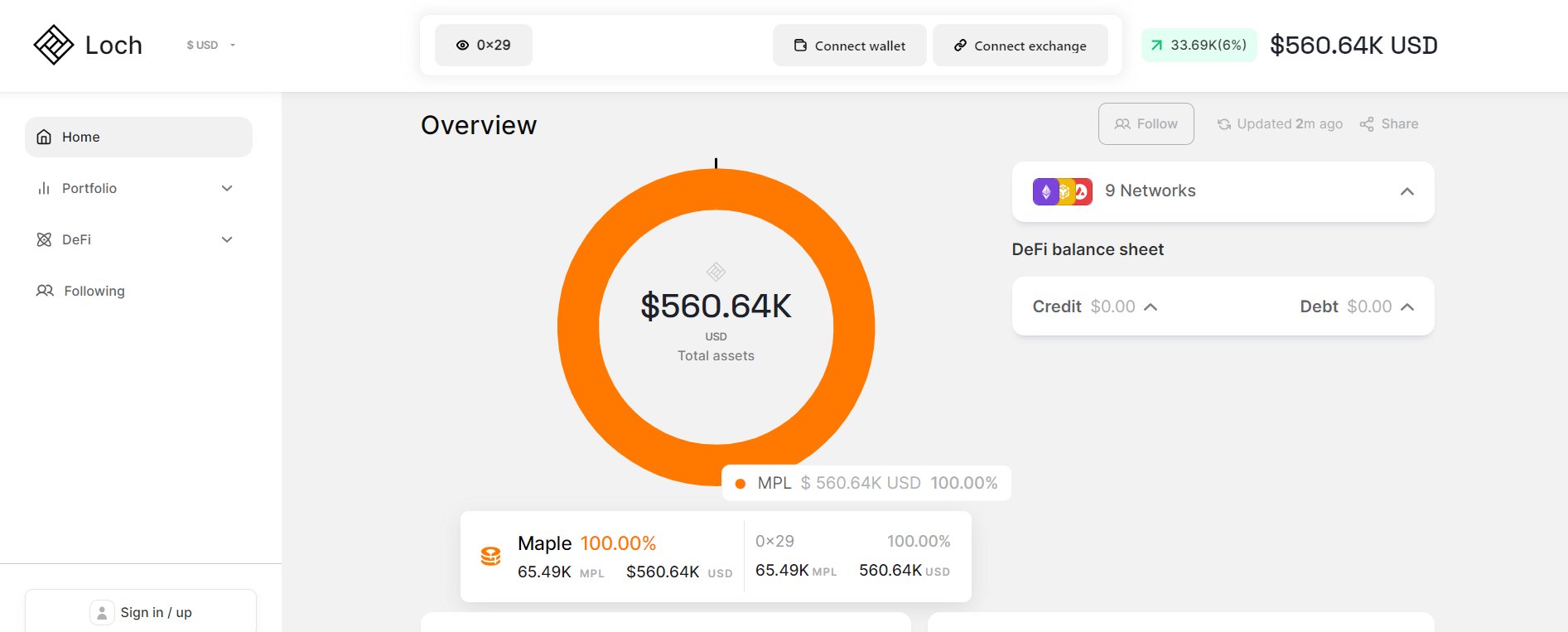
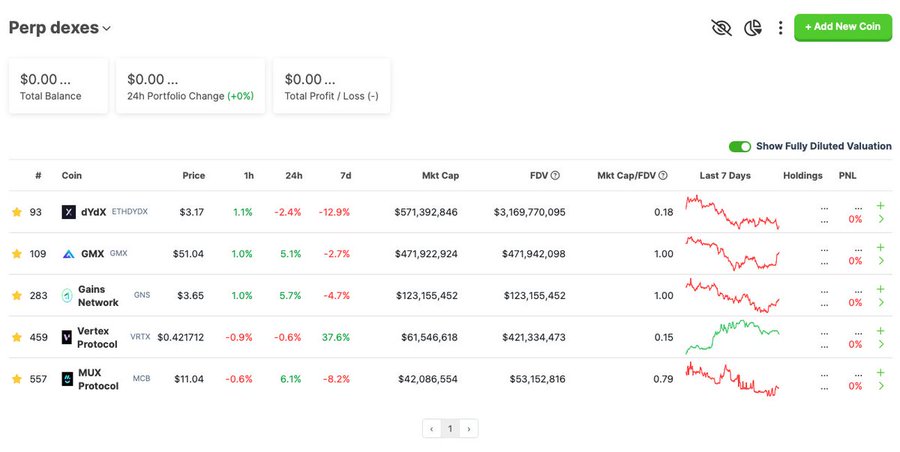
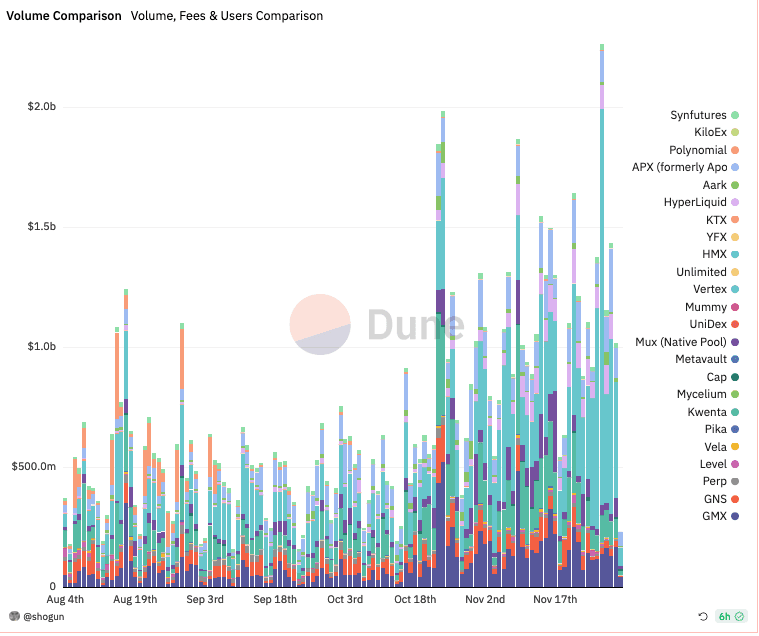
Not your keys, not your coins (The first rule of crypto)
Cryptocurrencies are stored in and transmitted to addresses. A Wallet address looks something like this.
0𝑥𝐷𝐴9𝑑𝑓𝐴130𝐷𝑓4𝑑𝐸4673𝑏89022𝐸𝐸50𝑓𝑓26𝑓6𝐸𝐴73𝐶𝑓
A wallet address is public. Anyone can view it, and anyone can send crypto assets to it. Think of a wallet address like an email address. Anyone who has your email can send you an email. Analogously, anyone who has your wallet address can send you cryptoassets.
However, there is more to a crypto wallet than just the address itself. A wallet address is a hashed version of your public key. Every public key is 256 bits long. The hashed version (your wallet address) is 160 bits long. The public key is used to ensure you are the owner of an address that can receive funds. The public key is also mathematically derived from your private key. But using reverse mathematics to derive the private key would take the world's most powerful supercomputer many trillion years to crack. Your private key is a randomly generated string (numbers and letters) of alphanumeric characters. A private key is always mathematically related to the wallet address but is impossible to reverse engineer thanks to strong encryption.
The private key is like the password to your email. You can’t send an email from a certain email address unless you have the password to access it. Similarly, you can’t send crypto from a wallet unless you have access to it via private keys (1).
If you didn’t understand the last few paragraphs or didn’t care to read them, don’t worry. The initial design for Bitcoin, while mathematically beautiful and cryptographically sound, wasn’t user friendly to say the least. Satoshi would be the first to say Mea Culpa to that. In addition to the technical complexity, having the masses safely store or remember their own private keys is asking a lot. This has led to hacking exploits that have cost crypto owners dearly. Furthermore, people often just forget and lose their private keys. Chainalysis estimates that 2.3 to 3.7 million Bitcoin has been lost. That’s over 100 billion dollars (as of writing in 2022).
Luckily, centralized exchanges like Coinbase, Binance, and Kraken innovated and delivered user friendly solutions that accelerated cryptoasset adoption. Most people purchase and store their crypto on centralized exchanges. They access their wallets the same way they log in to Facebook - using a username and password. If they forget their username or password, no problem. They can just reset it using their email address or phone number. Centralized exchanges will continue to play a massive role in the advent of global cryptoasset adoption. However, centralized exchanges are not without issues.
Centralized exchanges are still beholden to the governmental legislatures discussed in an earlier post - KYC, KYB, AML, OFAC, etc. It’s possible that governments crack down on centralized exchanges and force them to restrict certain individuals. Worse still, if cryptoassets start to rival USD in terms of market capitalization and volume settled or if smart contracts start to replace conventional corporate governance structure in a meaningful way, governments could forcefully legislate centralized exchanges to seize crypto assets or ban account access to vast swaths of the population.
This isn’t out of the question. President Franklin Roosevelt did this with gold in 1933 with Executive Order 6102 (2). President Jimmy Carter did this in 1979 with Executive Order 12170 (3). Canadian Prime Minister Justin Trudeau did this with protesting truckers earlier this year. I’m not picking sides and advocating whether Roosevelt, Carter, and Trudeau were correct or not. The point is that it’s possible for centralized crypto exchanges and custodians to capitulate and surrender individuals' crypto assets to the government.
“Not your keys, not your coins.”
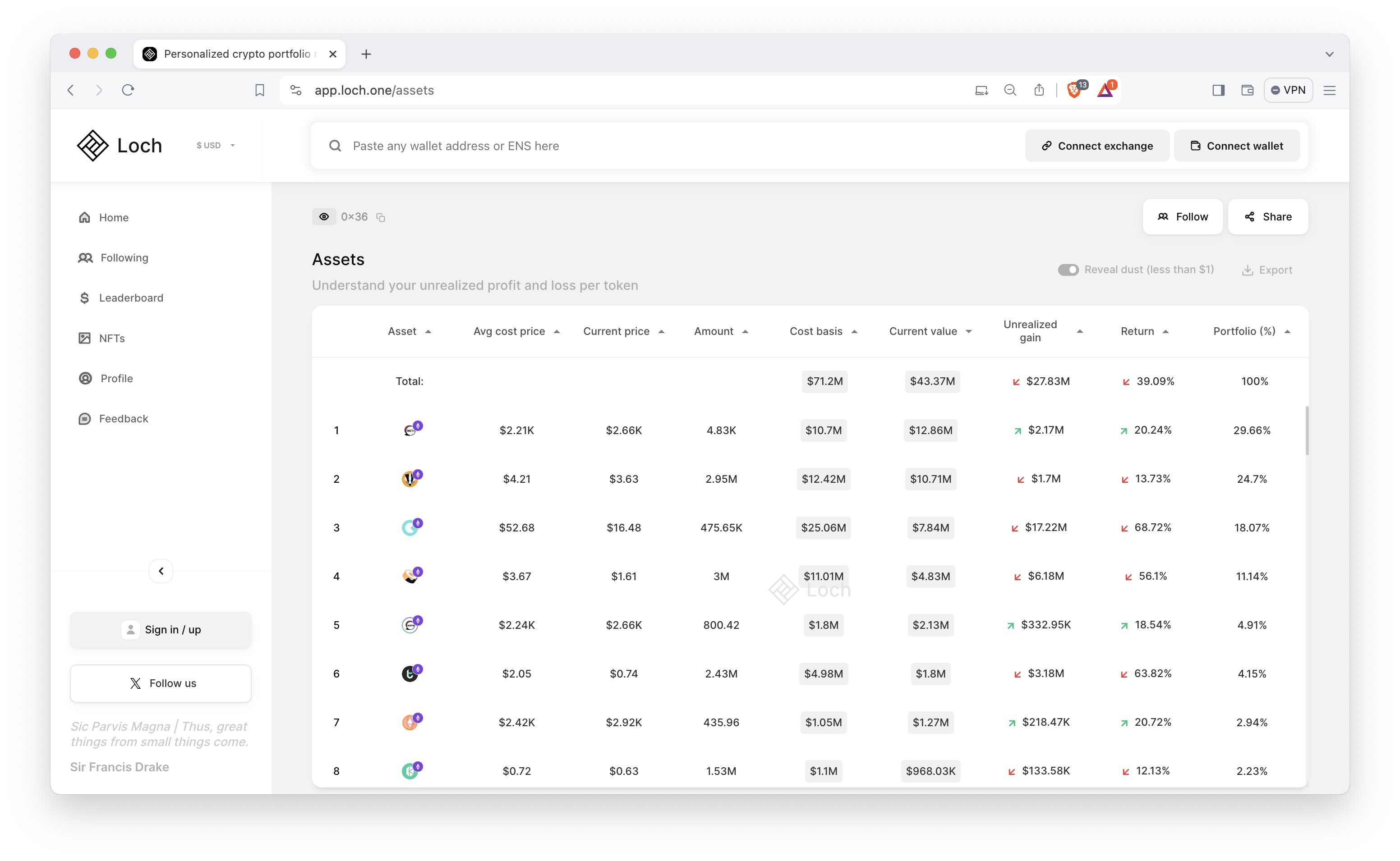
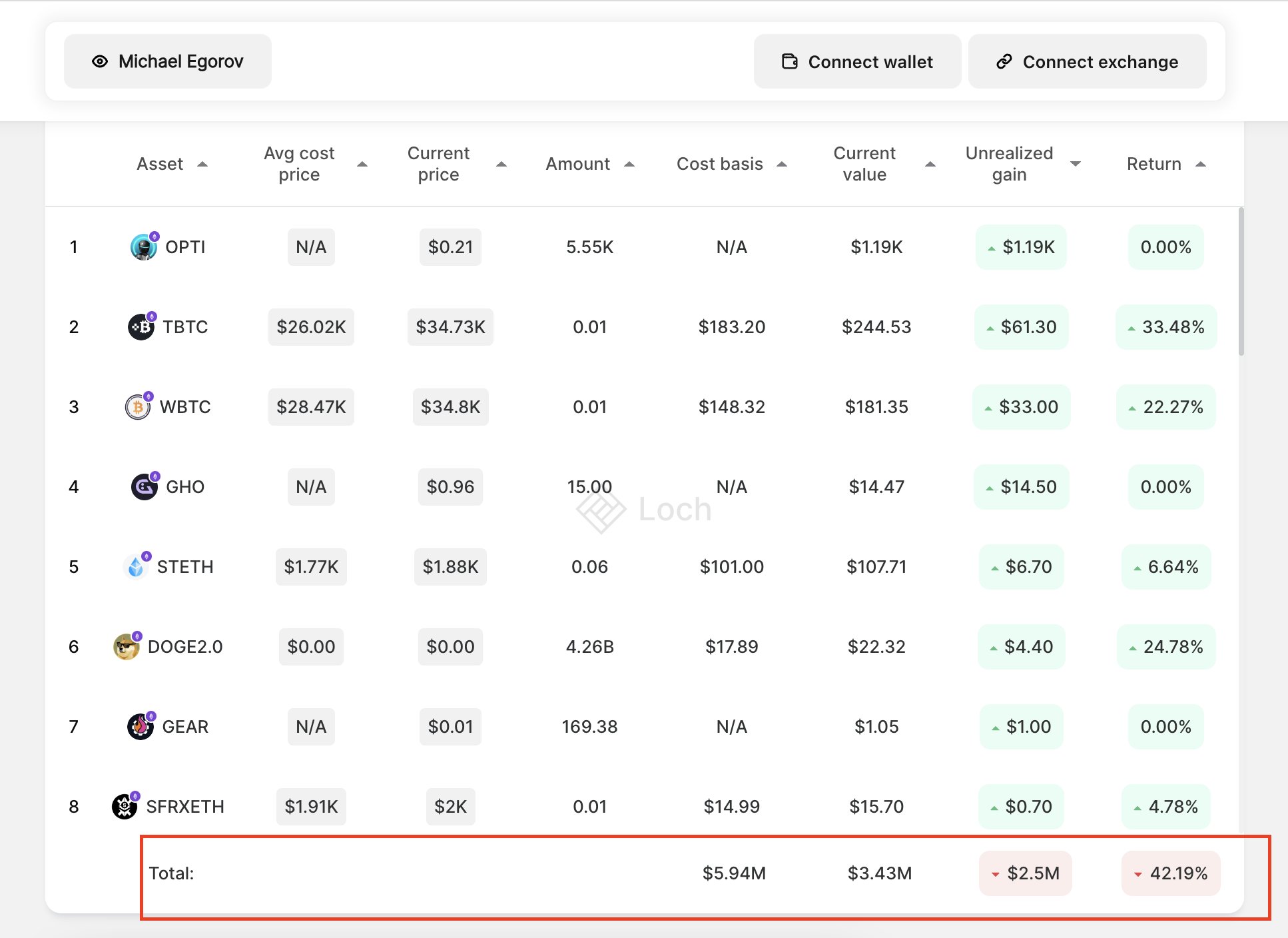
Colloquial crypto lore pithily states “not your keys, not your coins”. If you store your crypto on a centralized exchange, you don’t hold your own private keys. The exchange holds your private keys for you. You don’t hold or custody your crypto. You hold an IOU. You hold a mere representation of your currency. If you peruse your favorite blockchain using etherscan, blockchain.com’s explorer, solscan, chainalysis, nansen, dune, avaxscan etc. you’ll notice that centralized exchanges agglomerate all their customers' assets into a handful of public addresses and maintain internal ledgers for individual users. If you store your crypto on centralized exchanges, you’re susceptible to government mandated restriction or seizure.
I do acknowledge that owning cryptocurrency on centralized exchanges is better than not owning cryptocurrency at all. However, this isn’t self-sovereign money. Cryptoassets stored on centralized exchanges aren’t permissionless, seizure resistant, or decentralized.
Self-custody presents a better way
Today, one converts fiat to crypto using a centralized exchange or through an on-ramp like moonpay. However, if one wants to custody crypto themselves in a seizure resistant manner, they can transfer it to a self-custodial wallet. A self-custodial wallet is one where you hold your own private keys. No government, potentate, monarch, or God can seize your funds without your private keys. Self-custody is the quixotic zenith of seizure resistant wealth. There are two types of self-custody wallets: hot wallets and cold wallets.
A hot wallet is one connected to the internet. This can be a downloadable software application, a mere browser extension, or a mobile application. The most widely used self-custody hot wallets today are Metamask, Brave, Exodus, Phantom, Coinbase wallet. Hot wallets are free, quick to access, and easy to transact with. However, they could be susceptible to a higher percentage of successful hacks if the right precautions aren’t taken.
A cold wallet is typically not connected to the internet. Most hardware wallets are cold wallets and live on devices that look like USB sticks. Personal cold wallets cost anywhere between $50 to $200. They’re slower to use, but often more secure. Even when a hardware wallet is plugged into your computer or connected via Bluetooth and your computer is connected to the internet, the signing of transactions is done “in-device,” and only subsequently broadcast to the network via your computer’s internet connection. This “signature” allows you to assign ownership to the recipient of a cryptocurrency transaction. Your private keys never leave the device. Therefore, even if devious malware on your computer tried to steal your funds by maliciously “signing” a transaction initiated in your hardware wallet, it wouldn’t be the correct signature so the transaction wouldn’t go through. Cold wallets are less convenient than hot wallets because they require hardware but are generally much safer (4).
With a self-custodial hot or cold wallet, governments can't access your funds. Exchanges can't access your funds. No hacker par excellence can access your funds unless you make a mistake and do something stupid, or they get access to a quantum computer. In that case, Houston we have a much bigger problem. Nonetheless, you can even insure your cryptofunds against hacks using decentralized financial solutions like ArmorFi or Nexus Mutual. Self-custodial wallets are more closely aligned with the sovereign money Satoshi envisioned.
If self-custodial wallets are so great, why don’t more people adopt them? Why do only less than 10% of holders self-custody their crypto? Read our next piece on Problems with self-custody to learn more.
References:
Not your keys, not your coins (The first rule of crypto)
Cryptocurrencies are stored in and transmitted to addresses. A Wallet address looks something like this.
0𝑥𝐷𝐴9𝑑𝑓𝐴130𝐷𝑓4𝑑𝐸4673𝑏89022𝐸𝐸50𝑓𝑓26𝑓6𝐸𝐴73𝐶𝑓
A wallet address is public. Anyone can view it, and anyone can send crypto assets to it. Think of a wallet address like an email address. Anyone who has your email can send you an email. Analogously, anyone who has your wallet address can send you cryptoassets.
However, there is more to a crypto wallet than just the address itself. A wallet address is a hashed version of your public key. Every public key is 256 bits long. The hashed version (your wallet address) is 160 bits long. The public key is used to ensure you are the owner of an address that can receive funds. The public key is also mathematically derived from your private key. But using reverse mathematics to derive the private key would take the world's most powerful supercomputer many trillion years to crack. Your private key is a randomly generated string (numbers and letters) of alphanumeric characters. A private key is always mathematically related to the wallet address but is impossible to reverse engineer thanks to strong encryption.
The private key is like the password to your email. You can’t send an email from a certain email address unless you have the password to access it. Similarly, you can’t send crypto from a wallet unless you have access to it via private keys (1).
If you didn’t understand the last few paragraphs or didn’t care to read them, don’t worry. The initial design for Bitcoin, while mathematically beautiful and cryptographically sound, wasn’t user friendly to say the least. Satoshi would be the first to say Mea Culpa to that. In addition to the technical complexity, having the masses safely store or remember their own private keys is asking a lot. This has led to hacking exploits that have cost crypto owners dearly. Furthermore, people often just forget and lose their private keys. Chainalysis estimates that 2.3 to 3.7 million Bitcoin has been lost. That’s over 100 billion dollars (as of writing in 2022).
Luckily, centralized exchanges like Coinbase, Binance, and Kraken innovated and delivered user friendly solutions that accelerated cryptoasset adoption. Most people purchase and store their crypto on centralized exchanges. They access their wallets the same way they log in to Facebook - using a username and password. If they forget their username or password, no problem. They can just reset it using their email address or phone number. Centralized exchanges will continue to play a massive role in the advent of global cryptoasset adoption. However, centralized exchanges are not without issues.
Centralized exchanges are still beholden to the governmental legislatures discussed in an earlier post - KYC, KYB, AML, OFAC, etc. It’s possible that governments crack down on centralized exchanges and force them to restrict certain individuals. Worse still, if cryptoassets start to rival USD in terms of market capitalization and volume settled or if smart contracts start to replace conventional corporate governance structure in a meaningful way, governments could forcefully legislate centralized exchanges to seize crypto assets or ban account access to vast swaths of the population.
This isn’t out of the question. President Franklin Roosevelt did this with gold in 1933 with Executive Order 6102 (2). President Jimmy Carter did this in 1979 with Executive Order 12170 (3). Canadian Prime Minister Justin Trudeau did this with protesting truckers earlier this year. I’m not picking sides and advocating whether Roosevelt, Carter, and Trudeau were correct or not. The point is that it’s possible for centralized crypto exchanges and custodians to capitulate and surrender individuals' crypto assets to the government.
“Not your keys, not your coins.”
Colloquial crypto lore pithily states “not your keys, not your coins”. If you store your crypto on a centralized exchange, you don’t hold your own private keys. The exchange holds your private keys for you. You don’t hold or custody your crypto. You hold an IOU. You hold a mere representation of your currency. If you peruse your favorite blockchain using etherscan, blockchain.com’s explorer, solscan, chainalysis, nansen, dune, avaxscan etc. you’ll notice that centralized exchanges agglomerate all their customers' assets into a handful of public addresses and maintain internal ledgers for individual users. If you store your crypto on centralized exchanges, you’re susceptible to government mandated restriction or seizure.
I do acknowledge that owning cryptocurrency on centralized exchanges is better than not owning cryptocurrency at all. However, this isn’t self-sovereign money. Cryptoassets stored on centralized exchanges aren’t permissionless, seizure resistant, or decentralized.
Self-custody presents a better way
Today, one converts fiat to crypto using a centralized exchange or through an on-ramp like moonpay. However, if one wants to custody crypto themselves in a seizure resistant manner, they can transfer it to a self-custodial wallet. A self-custodial wallet is one where you hold your own private keys. No government, potentate, monarch, or God can seize your funds without your private keys. Self-custody is the quixotic zenith of seizure resistant wealth. There are two types of self-custody wallets: hot wallets and cold wallets.
A hot wallet is one connected to the internet. This can be a downloadable software application, a mere browser extension, or a mobile application. The most widely used self-custody hot wallets today are Metamask, Brave, Exodus, Phantom, Coinbase wallet. Hot wallets are free, quick to access, and easy to transact with. However, they could be susceptible to a higher percentage of successful hacks if the right precautions aren’t taken.
A cold wallet is typically not connected to the internet. Most hardware wallets are cold wallets and live on devices that look like USB sticks. Personal cold wallets cost anywhere between $50 to $200. They’re slower to use, but often more secure. Even when a hardware wallet is plugged into your computer or connected via Bluetooth and your computer is connected to the internet, the signing of transactions is done “in-device,” and only subsequently broadcast to the network via your computer’s internet connection. This “signature” allows you to assign ownership to the recipient of a cryptocurrency transaction. Your private keys never leave the device. Therefore, even if devious malware on your computer tried to steal your funds by maliciously “signing” a transaction initiated in your hardware wallet, it wouldn’t be the correct signature so the transaction wouldn’t go through. Cold wallets are less convenient than hot wallets because they require hardware but are generally much safer (4).
With a self-custodial hot or cold wallet, governments can't access your funds. Exchanges can't access your funds. No hacker par excellence can access your funds unless you make a mistake and do something stupid, or they get access to a quantum computer. In that case, Houston we have a much bigger problem. Nonetheless, you can even insure your cryptofunds against hacks using decentralized financial solutions like ArmorFi or Nexus Mutual. Self-custodial wallets are more closely aligned with the sovereign money Satoshi envisioned.
If self-custodial wallets are so great, why don’t more people adopt them? Why do only less than 10% of holders self-custody their crypto? Read our next piece on Problems with self-custody to learn more.
References:
Continue reading
Continue reading

Not your keys, not your coins (The first rule of crypto)
Dec 14, 2022

Not your keys, not your coins (The first rule of crypto)
Dec 14, 2022