Mastering Crypto Security: Practices for Safeguarding Your Assets
In the fast-paced realm of cryptocurrencies, security is paramount. The decentralized and digital nature of these assets necessitates proactive measures to protect against potential threats. Whether you're a seasoned investor or just stepping into the world of crypto, adopting best practices can significantly mitigate risks and enhance the security of your holdings since this digital realm is not devoid of risks; in fact, it's fraught with intricate security challenges that demand vigilant measures to safeguard holdings against sophisticated cyber threats.
The cornerstone of navigating this domain effectively lies in understanding and implementing robust security practices. From steering clear of phishing attempts to leveraging the tradeoffs between cold and hot wallets, each step toward fortifying crypto security plays a pivotal role in safeguarding valuable assets.
This comprehensive guide dives deep into the intricacies of securing your crypto holdings, emphasizing best practices, nuanced differences between wallet types, and the critical tradeoffs between heightened security and increased accessibility. By delving into these layers of protection, you'll gain a holistic understanding of how to minimize risks and fortify your defenses in the captivating yet complex world of cryptocurrencies.
Let’s explore the multifaceted aspects of crypto security, unraveling the best practices and tradeoffs that underpin the protection of digital assets. This guide aims to equip you with the knowledge and strategies needed to navigate the ever-shifting landscape of crypto security with confidence and prudence.
Let's discuss the importance of vigilance:
Biometric Authentication: Utilizing biometric authentication, such as fingerprint or facial recognition, can add an extra layer of security to your crypto wallets. This advanced form of verification ensures that only authorized users can access their accounts, significantly reducing the risk of unauthorized access.
Secure Password Management: Creating strong, unique passwords for each crypto-related account is crucial. Consider using reputable password managers to generate and securely store complex passwords. Avoid using easily guessable information like birthdays or common phrases.
Utilize Multi-Signature Wallets: Multi-signature wallets require multiple private keys to authorize transactions. For instance, a wallet might require two out of three private keys to sign off on a transaction, enhancing security by distributing control among multiple parties or devices.
Conduct Security Audits: Regularly auditing your security measures can identify vulnerabilities before they're exploited. Consider engaging security professionals or using reputable security auditing tools to assess your systems, wallets, and overall infrastructure.
Enable Whitelisting and Address Verification: Implementing whitelisting features allows users to specify which addresses they can send funds to or receive funds from. This restriction prevents unauthorized transactions to unknown or unverified addresses, adding an extra layer of protection against fraudulent activities.
Monitor Account Activity: Stay vigilant by monitoring your account activity and transaction history regularly. Look out for any suspicious or unfamiliar transactions that could indicate unauthorized access or potential security breaches.
Secure Network and Device Practices: Besides avoiding public Wi-Fi, ensure that your home network and devices are secured with up-to-date antivirus software, firewalls, and encryption. Regularly scan devices for malware or potential security threats.
Stay informed and educated: The crypto landscape is dynamic, with new security threats emerging constantly. Stay updated with the latest security practices, trends, and news within the crypto community. Engage with reputable sources, forums, and communities to gain insights and share experiences with other users.
Implementing Cryptographic Techniques: Explore cryptographic techniques like encryption and hashing to secure your sensitive information. Encryption scrambles data, making it unreadable without the decryption key. Hashing converts data into a fixed-size string, ensuring data integrity and authenticity.
Secure Physical Storage: For those utilizing hardware wallets or paper wallets, secure physical storage is essential. Store hardware wallets in a safe and secure location, preferably in a fireproof and waterproof container. Likewise, protect paper wallets from physical damage or theft by storing them in a secure location.
Secure Social Media and Online Presence: Be cautious about sharing too much information about your crypto holdings or activities on social media or public forums. Limiting exposure to personal details related to your crypto holdings can mitigate the risk of targeted attacks or social engineering attempts.
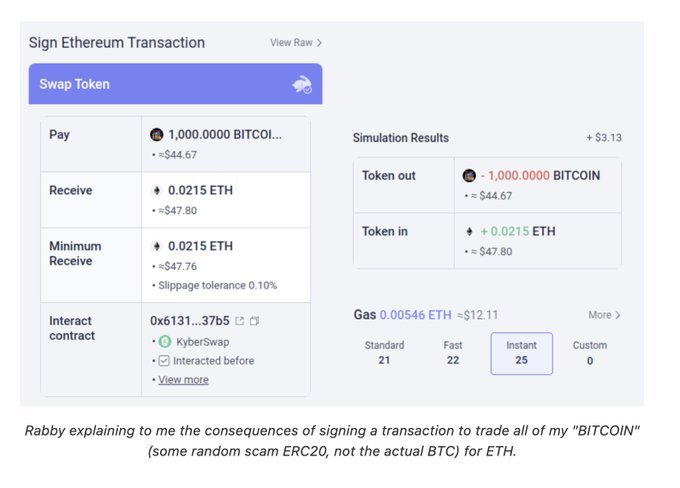
Avoiding Phishy Links: Cybercriminals often employ phishing tactics to lure unsuspecting users into divulging sensitive information. Avoid clicking on suspicious links from email, social media, or other platforms. Scammers may mimic legitimate websites or services to steal login credentials or compromise wallets.
Diversifying Wallets: Relying on a single wallet could expose you to substantial risk. Diversification across multiple wallets ensures that a compromise on one doesn't lead to the loss of your entire portfolio. Consider using different types of wallets, each serving a unique purpose.
Understanding the difference between cold and hot wallets is crucial in comprehending the tradeoffs associated with each and making informed decisions about securing your cryptocurrency.
Cold Wallets: Cold wallets refer to offline storage solutions that store cryptocurrency keys (public and private) in a manner disconnected from the internet. They come in various forms, including hardware wallets, paper wallets, and offline software wallets.
Offline Storage: The primary advantage of cold wallets is their isolation from online networks, reducing the risk of cyberattacks or hacking attempts.
Resistance to Online Threats: Since they aren't connected to the internet, cold wallets are immune to many online threats such as malware or phishing attacks.
Physical Security: Hardware wallets and paper wallets offer physical security, ensuring that access to your funds requires direct physical access to the wallet device or paper containing keys.
Tradeoffs:
Limited Accessibility: Cold wallets are less convenient for frequent transactions or quick access to funds due to their offline nature.
Potential for Physical Loss: Inadvertent damage, loss, or theft of hardware wallets or paper containing private keys poses a risk of losing access to your funds permanently.
Hot Wallets: Hot wallets are online or internet-connected storage solutions used for storing cryptocurrency keys. They encompass various forms, including mobile wallets, desktop wallets, and online wallets provided by exchanges.
Convenience Features:
Accessibility: Hot wallets offer instant access to funds, making them convenient for everyday transactions or trading activities.
Ease of Use: They provide user-friendly interfaces and quick access to funds, suitable for active traders and frequent users.
Tradeoffs:
Increased Vulnerability: Being connected to the internet exposes hot wallets to online threats such as hacking, phishing, malware, and other cyberattacks.
Security Risks: Compared to cold wallets, hot wallets have a higher risk of being compromised due to their online presence and potential vulnerabilities in software or platforms.
Dependence on Service Providers: Online wallets hosted by exchanges or third-party platforms mean that the security of your funds relies on the security measures implemented by these service providers.
The Tradeoff Between Cold and Hot Wallets:
Security vs. Accessibility: The fundamental tradeoff between cold and hot wallets revolves around security and accessibility. Cold wallets prioritize security by keeping assets offline, minimizing the risk of hacking, while hot wallets prioritize accessibility for easier and quicker transactions but are inherently more vulnerable to online threats.
Usage Considerations: For long-term storage or large amounts of cryptocurrency, cold wallets are recommended due to their high security features. Hot wallets, on the other hand, are suitable for smaller amounts or assets intended for regular trading or spending due to their convenience and accessibility.
Selecting the right wallet type depends on individual preferences, risk tolerance, and intended usage of cryptocurrencies. For maximum security, many users opt for a combination of both cold and hot wallets, utilizing cold storage for long-term holding and hot wallets for everyday transactions. Understanding the tradeoffs allows users to strike a balance between security and accessibility based on their specific needs in the dynamic landscape of cryptocurrency.
Maximizing Security with Best Practices
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring multiple forms of authentication to access your accounts. Enabling features like SMS authentication, authenticator apps, or hardware keys significantly bolsters security.
Regular Software Updates: Keeping your wallet software and devices updated is crucial. Software updates often include security patches that address known vulnerabilities, reducing the risk of exploitation by attackers.
Backup and Recovery: Always create backups of your wallet's private keys or seed phrases. Store these backups securely in multiple offline locations to ensure recovery in case of loss or damage to your primary wallet.
Use Reputable Exchanges and Services: When conducting transactions or utilizing crypto-related services, opt for reputable and well-established platforms. Research and verify the credibility and security measures of exchanges and services before entrusting them with your assets.
Practicing Caution with Public Wi-Fi and Devices: Avoid accessing your crypto wallets or making transactions using public Wi-Fi networks or unsecured devices. These networks might be compromised, potentially exposing your sensitive information to malicious actors.
Conclusion
In the ever-evolving landscape of cryptocurrency, safeguarding your assets demands constant vigilance and adherence to best security practices. Remember, the responsibility for securing your crypto assets ultimately lies with you. Embrace these best practices and empower yourself to navigate the crypto space with confidence and minimize risk. By adopting a holistic approach to crypto security and integrating these additional best practices, individuals can significantly enhance the protection of their crypto assets. Constant vigilance, staying informed, employing advanced security measures, and maintaining a proactive mindset are paramount to safeguarding against the evolving threats in the cryptosphere. Implementing these strategies not only fortifies your defenses but also provides peace of mind in navigating the exciting world of cryptocurrencies.
Mastering Crypto Security: Practices for Safeguarding Your Assets
In the fast-paced realm of cryptocurrencies, security is paramount. The decentralized and digital nature of these assets necessitates proactive measures to protect against potential threats. Whether you're a seasoned investor or just stepping into the world of crypto, adopting best practices can significantly mitigate risks and enhance the security of your holdings since this digital realm is not devoid of risks; in fact, it's fraught with intricate security challenges that demand vigilant measures to safeguard holdings against sophisticated cyber threats.
The cornerstone of navigating this domain effectively lies in understanding and implementing robust security practices. From steering clear of phishing attempts to leveraging the tradeoffs between cold and hot wallets, each step toward fortifying crypto security plays a pivotal role in safeguarding valuable assets.
This comprehensive guide dives deep into the intricacies of securing your crypto holdings, emphasizing best practices, nuanced differences between wallet types, and the critical tradeoffs between heightened security and increased accessibility. By delving into these layers of protection, you'll gain a holistic understanding of how to minimize risks and fortify your defenses in the captivating yet complex world of cryptocurrencies.
Let’s explore the multifaceted aspects of crypto security, unraveling the best practices and tradeoffs that underpin the protection of digital assets. This guide aims to equip you with the knowledge and strategies needed to navigate the ever-shifting landscape of crypto security with confidence and prudence.
Let's discuss the importance of vigilance:
Biometric Authentication: Utilizing biometric authentication, such as fingerprint or facial recognition, can add an extra layer of security to your crypto wallets. This advanced form of verification ensures that only authorized users can access their accounts, significantly reducing the risk of unauthorized access.
Secure Password Management: Creating strong, unique passwords for each crypto-related account is crucial. Consider using reputable password managers to generate and securely store complex passwords. Avoid using easily guessable information like birthdays or common phrases.
Utilize Multi-Signature Wallets: Multi-signature wallets require multiple private keys to authorize transactions. For instance, a wallet might require two out of three private keys to sign off on a transaction, enhancing security by distributing control among multiple parties or devices.
Conduct Security Audits: Regularly auditing your security measures can identify vulnerabilities before they're exploited. Consider engaging security professionals or using reputable security auditing tools to assess your systems, wallets, and overall infrastructure.
Enable Whitelisting and Address Verification: Implementing whitelisting features allows users to specify which addresses they can send funds to or receive funds from. This restriction prevents unauthorized transactions to unknown or unverified addresses, adding an extra layer of protection against fraudulent activities.
Monitor Account Activity: Stay vigilant by monitoring your account activity and transaction history regularly. Look out for any suspicious or unfamiliar transactions that could indicate unauthorized access or potential security breaches.
Secure Network and Device Practices: Besides avoiding public Wi-Fi, ensure that your home network and devices are secured with up-to-date antivirus software, firewalls, and encryption. Regularly scan devices for malware or potential security threats.
Stay informed and educated: The crypto landscape is dynamic, with new security threats emerging constantly. Stay updated with the latest security practices, trends, and news within the crypto community. Engage with reputable sources, forums, and communities to gain insights and share experiences with other users.
Implementing Cryptographic Techniques: Explore cryptographic techniques like encryption and hashing to secure your sensitive information. Encryption scrambles data, making it unreadable without the decryption key. Hashing converts data into a fixed-size string, ensuring data integrity and authenticity.
Secure Physical Storage: For those utilizing hardware wallets or paper wallets, secure physical storage is essential. Store hardware wallets in a safe and secure location, preferably in a fireproof and waterproof container. Likewise, protect paper wallets from physical damage or theft by storing them in a secure location.
Secure Social Media and Online Presence: Be cautious about sharing too much information about your crypto holdings or activities on social media or public forums. Limiting exposure to personal details related to your crypto holdings can mitigate the risk of targeted attacks or social engineering attempts.
Avoiding Phishy Links: Cybercriminals often employ phishing tactics to lure unsuspecting users into divulging sensitive information. Avoid clicking on suspicious links from email, social media, or other platforms. Scammers may mimic legitimate websites or services to steal login credentials or compromise wallets.
Diversifying Wallets: Relying on a single wallet could expose you to substantial risk. Diversification across multiple wallets ensures that a compromise on one doesn't lead to the loss of your entire portfolio. Consider using different types of wallets, each serving a unique purpose.
Understanding the difference between cold and hot wallets is crucial in comprehending the tradeoffs associated with each and making informed decisions about securing your cryptocurrency.
Cold Wallets: Cold wallets refer to offline storage solutions that store cryptocurrency keys (public and private) in a manner disconnected from the internet. They come in various forms, including hardware wallets, paper wallets, and offline software wallets.
Offline Storage: The primary advantage of cold wallets is their isolation from online networks, reducing the risk of cyberattacks or hacking attempts.
Resistance to Online Threats: Since they aren't connected to the internet, cold wallets are immune to many online threats such as malware or phishing attacks.
Physical Security: Hardware wallets and paper wallets offer physical security, ensuring that access to your funds requires direct physical access to the wallet device or paper containing keys.
Tradeoffs:
Limited Accessibility: Cold wallets are less convenient for frequent transactions or quick access to funds due to their offline nature.
Potential for Physical Loss: Inadvertent damage, loss, or theft of hardware wallets or paper containing private keys poses a risk of losing access to your funds permanently.
Hot Wallets: Hot wallets are online or internet-connected storage solutions used for storing cryptocurrency keys. They encompass various forms, including mobile wallets, desktop wallets, and online wallets provided by exchanges.
Convenience Features:
Accessibility: Hot wallets offer instant access to funds, making them convenient for everyday transactions or trading activities.
Ease of Use: They provide user-friendly interfaces and quick access to funds, suitable for active traders and frequent users.
Tradeoffs:
Increased Vulnerability: Being connected to the internet exposes hot wallets to online threats such as hacking, phishing, malware, and other cyberattacks.
Security Risks: Compared to cold wallets, hot wallets have a higher risk of being compromised due to their online presence and potential vulnerabilities in software or platforms.
Dependence on Service Providers: Online wallets hosted by exchanges or third-party platforms mean that the security of your funds relies on the security measures implemented by these service providers.
The Tradeoff Between Cold and Hot Wallets:
Security vs. Accessibility: The fundamental tradeoff between cold and hot wallets revolves around security and accessibility. Cold wallets prioritize security by keeping assets offline, minimizing the risk of hacking, while hot wallets prioritize accessibility for easier and quicker transactions but are inherently more vulnerable to online threats.
Usage Considerations: For long-term storage or large amounts of cryptocurrency, cold wallets are recommended due to their high security features. Hot wallets, on the other hand, are suitable for smaller amounts or assets intended for regular trading or spending due to their convenience and accessibility.
Selecting the right wallet type depends on individual preferences, risk tolerance, and intended usage of cryptocurrencies. For maximum security, many users opt for a combination of both cold and hot wallets, utilizing cold storage for long-term holding and hot wallets for everyday transactions. Understanding the tradeoffs allows users to strike a balance between security and accessibility based on their specific needs in the dynamic landscape of cryptocurrency.
Maximizing Security with Best Practices
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring multiple forms of authentication to access your accounts. Enabling features like SMS authentication, authenticator apps, or hardware keys significantly bolsters security.
Regular Software Updates: Keeping your wallet software and devices updated is crucial. Software updates often include security patches that address known vulnerabilities, reducing the risk of exploitation by attackers.
Backup and Recovery: Always create backups of your wallet's private keys or seed phrases. Store these backups securely in multiple offline locations to ensure recovery in case of loss or damage to your primary wallet.
Use Reputable Exchanges and Services: When conducting transactions or utilizing crypto-related services, opt for reputable and well-established platforms. Research and verify the credibility and security measures of exchanges and services before entrusting them with your assets.
Practicing Caution with Public Wi-Fi and Devices: Avoid accessing your crypto wallets or making transactions using public Wi-Fi networks or unsecured devices. These networks might be compromised, potentially exposing your sensitive information to malicious actors.
Conclusion
In the ever-evolving landscape of cryptocurrency, safeguarding your assets demands constant vigilance and adherence to best security practices. Remember, the responsibility for securing your crypto assets ultimately lies with you. Embrace these best practices and empower yourself to navigate the crypto space with confidence and minimize risk. By adopting a holistic approach to crypto security and integrating these additional best practices, individuals can significantly enhance the protection of their crypto assets. Constant vigilance, staying informed, employing advanced security measures, and maintaining a proactive mindset are paramount to safeguarding against the evolving threats in the cryptosphere. Implementing these strategies not only fortifies your defenses but also provides peace of mind in navigating the exciting world of cryptocurrencies.
Continue reading
Continue reading
Mastering Crypto Security: Practices for Safeguarding Your Assets
Dec 9, 2023

Mastering Crypto Security: Practices for Safeguarding Your Assets
Dec 9, 2023