Ledger’s New Hardware Wallet Recovery Update: A Step Forward or A New Vulnerability?
Introduction:
Ledger has recently released a groundbreaking update aimed at simplifying the user experience (UX) for its hardware wallets. This enhancement is geared towards resolving the ubiquitous "mom test," a term coined to represent the general user's ability to operate a piece of technology intuitively. Simplifying the interface and user experience of crypto hardware wallets could potentially result in broader adoption, augmenting the metcalfian network effects within the cryptocurrency ecosystem.
However, with new features come new vulnerabilities. This article explores Ledger's update, its impact on user experience and adoption, and the potential security concerns it raises.
The Update: A Leap Towards Simplified UX:
In an era marked by the acceleration of digital currency utilization, Ledger’s update is seen as a way to bridge the gap between complex technology and user-friendly interfaces. This is imperative as the essence of mass adoption lies in the hands of everyday users passing the "mom test", enabling a broader range of individuals to navigate and utilize cryptocurrency hardware wallets without extensive prior knowledge.
The crypto ecosystem thrives on network effects, described by Metcalfe’s law, asserting the value of a network is proportional to the square of the number of connected users. In this context, broadening user accessibility could lead to an enhanced network effect, solidifying the crypto ecosystem's foundation and expanding its reach.
Breaking Down the Update:
The new update for Ledger Nano X introduces a social recovery feature for your seed phrase. It involves encrypting the seed in three shards, sent to different entities. These entities can then reconstruct the seed post-ID verification, if necessary.
This new feature may have its benefits in terms of recovery, but it’s also subject to criticism. It introduces a layer of third-party trust which fundamentally opposes the essence of self-custodial wallets — a core proposition in the world of decentralized currencies.
Potential Vulnerabilities:
While sharding keys is seen as a positive step in enhancing security, the introduction of "ID verification" can be relatively insecure. There have been numerous instances of high-profile SIM jacking and identity theft, raising red flags around this new approach.
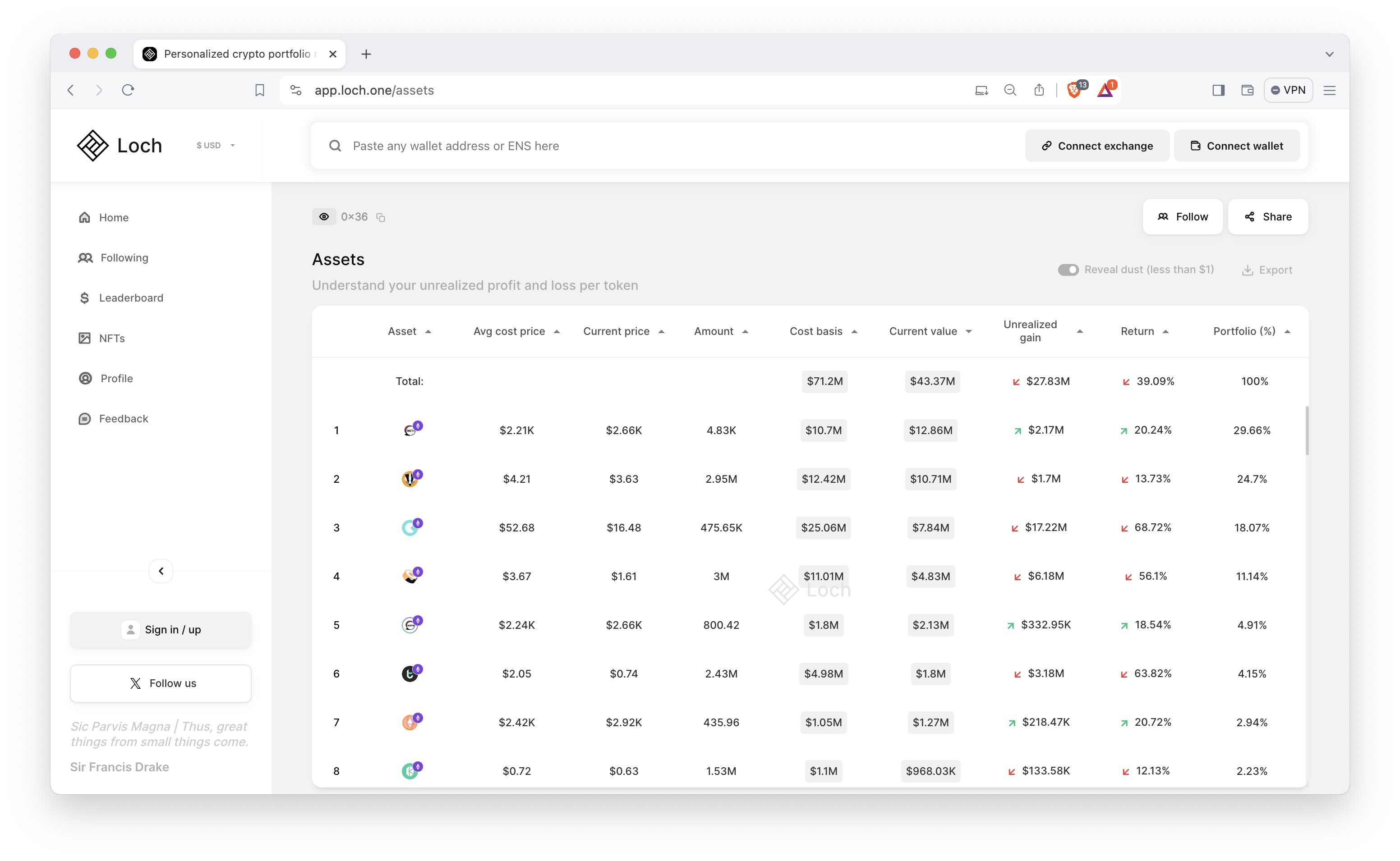
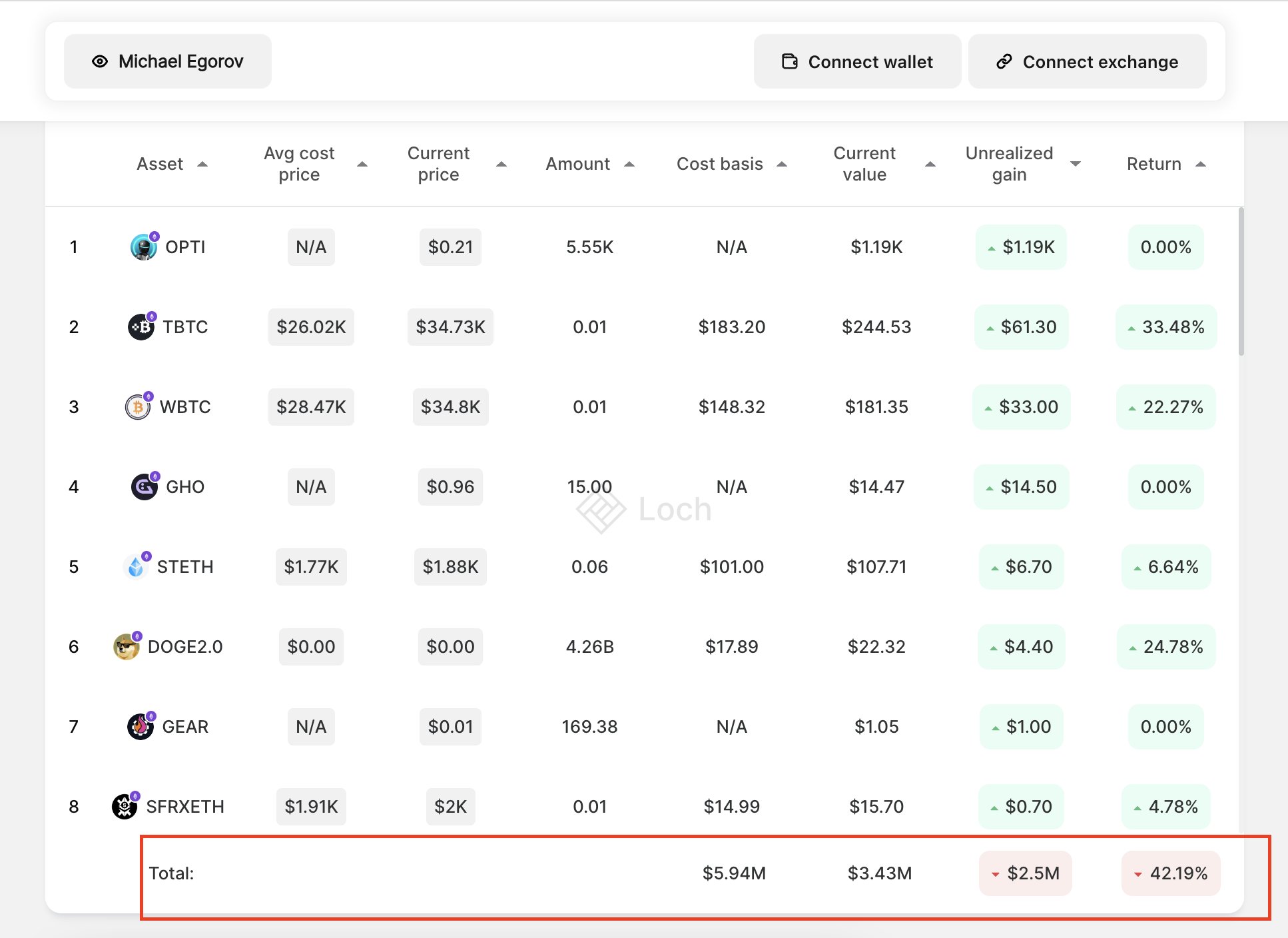
Prithvir, the Co-Founder, and CEO of Loch Chain and a former associate of Morgan Stanley and Duke University, has been openly critical about this new update. He points out that this feature opens up a new attack vector, waiting to be exploited. He further implies that users could be at risk due to the relative insecurity of ID verification methods in place. Prithvir has opted to continue using Trezor, citing concerns over the newfound layer of third-party trust introduced by Ledger.
Mudit Gupta also shared his reservations about this feature, stating that it is a “horrendous idea,” urging users not to enable this feature, due to the potential security concerns it presents. He highlighted that introducing a third party can jeopardize the very autonomy and security that self-custodial wallets aim to provide.
Weighing User Experience Against Security:
It’s paramount to weigh the benefits of simplified UX against the potential security pitfalls. Enhanced user experience could indeed solve the "mom test" and be instrumental in driving wider adoption of cryptocurrencies, allowing more users to access and leverage the decentralized finance (DeFi) ecosystem, enhancing its metcalfian network effects.
However, simplifying user experience should not compromise the security and integrity of the user’s assets. Any compromise on security could potentially lead to exploitation and loss of assets, undermining user trust in the technology, which can significantly hamper the road to mass adoption.
The Balance Between Trust and Autonomy:
Self-custodial wallets are pivotal in the crypto landscape due to their ability to provide users with control and autonomy over their assets. Introducing a third party, however innocuous it might seem, could erode this autonomy and introduce elements of trust that are antithetical to the decentralized essence of blockchain and cryptocurrencies.
In the age of rampant cyber-attacks and security breaches, the use of ID verification can be precarious. The incessant occurrence of identity theft and SIM jacking emphasizes the need for robust security mechanisms, even as companies endeavor to simplify and enhance user experiences.
Conclusion:
The new update from Ledger underscores the ongoing tug-of-war between user experience and security within the crypto ecosystem. The aim to resolve the “mom test” is commendable and indeed much needed for the widespread adoption of crypto technologies. However, it’s crucial to tread this path carefully, ensuring user autonomy and security aren’t sacrificed on the altar of simplicity and convenience.
As the crypto landscape continues to evolve, it’s essential for industry leaders and developers to strike a harmonious balance between making technologies user-friendly and maintaining the rigorous security standards essential for protecting user assets and trust.
In a landscape as dynamic and rapidly evolving as cryptocurrency, discussions surrounding advancements and their accompanying challenges are not just inevitable but necessary. As users and stakeholders in this ecosystem, it’s crucial to stay informed, weigh the pros and cons, and make discerning choices that align with individual needs and the foundational principles of decentralized technologies.
For more detailed insights on this topic and ongoing discussions, stay connected with relevant contributors and keep abreast with the evolving trends and updates within the crypto world.
Remember, the journey of cryptocurrency is as much about innovation and adoption as it is about learning and making informed decisions every step of the way.
Ledger’s New Hardware Wallet Recovery Update: A Step Forward or A New Vulnerability?
Introduction:
Ledger has recently released a groundbreaking update aimed at simplifying the user experience (UX) for its hardware wallets. This enhancement is geared towards resolving the ubiquitous "mom test," a term coined to represent the general user's ability to operate a piece of technology intuitively. Simplifying the interface and user experience of crypto hardware wallets could potentially result in broader adoption, augmenting the metcalfian network effects within the cryptocurrency ecosystem.
However, with new features come new vulnerabilities. This article explores Ledger's update, its impact on user experience and adoption, and the potential security concerns it raises.
The Update: A Leap Towards Simplified UX:
In an era marked by the acceleration of digital currency utilization, Ledger’s update is seen as a way to bridge the gap between complex technology and user-friendly interfaces. This is imperative as the essence of mass adoption lies in the hands of everyday users passing the "mom test", enabling a broader range of individuals to navigate and utilize cryptocurrency hardware wallets without extensive prior knowledge.
The crypto ecosystem thrives on network effects, described by Metcalfe’s law, asserting the value of a network is proportional to the square of the number of connected users. In this context, broadening user accessibility could lead to an enhanced network effect, solidifying the crypto ecosystem's foundation and expanding its reach.
Breaking Down the Update:
The new update for Ledger Nano X introduces a social recovery feature for your seed phrase. It involves encrypting the seed in three shards, sent to different entities. These entities can then reconstruct the seed post-ID verification, if necessary.
This new feature may have its benefits in terms of recovery, but it’s also subject to criticism. It introduces a layer of third-party trust which fundamentally opposes the essence of self-custodial wallets — a core proposition in the world of decentralized currencies.
Potential Vulnerabilities:
While sharding keys is seen as a positive step in enhancing security, the introduction of "ID verification" can be relatively insecure. There have been numerous instances of high-profile SIM jacking and identity theft, raising red flags around this new approach.
Prithvir, the Co-Founder, and CEO of Loch Chain and a former associate of Morgan Stanley and Duke University, has been openly critical about this new update. He points out that this feature opens up a new attack vector, waiting to be exploited. He further implies that users could be at risk due to the relative insecurity of ID verification methods in place. Prithvir has opted to continue using Trezor, citing concerns over the newfound layer of third-party trust introduced by Ledger.
Mudit Gupta also shared his reservations about this feature, stating that it is a “horrendous idea,” urging users not to enable this feature, due to the potential security concerns it presents. He highlighted that introducing a third party can jeopardize the very autonomy and security that self-custodial wallets aim to provide.
Weighing User Experience Against Security:
It’s paramount to weigh the benefits of simplified UX against the potential security pitfalls. Enhanced user experience could indeed solve the "mom test" and be instrumental in driving wider adoption of cryptocurrencies, allowing more users to access and leverage the decentralized finance (DeFi) ecosystem, enhancing its metcalfian network effects.
However, simplifying user experience should not compromise the security and integrity of the user’s assets. Any compromise on security could potentially lead to exploitation and loss of assets, undermining user trust in the technology, which can significantly hamper the road to mass adoption.
The Balance Between Trust and Autonomy:
Self-custodial wallets are pivotal in the crypto landscape due to their ability to provide users with control and autonomy over their assets. Introducing a third party, however innocuous it might seem, could erode this autonomy and introduce elements of trust that are antithetical to the decentralized essence of blockchain and cryptocurrencies.
In the age of rampant cyber-attacks and security breaches, the use of ID verification can be precarious. The incessant occurrence of identity theft and SIM jacking emphasizes the need for robust security mechanisms, even as companies endeavor to simplify and enhance user experiences.
Conclusion:
The new update from Ledger underscores the ongoing tug-of-war between user experience and security within the crypto ecosystem. The aim to resolve the “mom test” is commendable and indeed much needed for the widespread adoption of crypto technologies. However, it’s crucial to tread this path carefully, ensuring user autonomy and security aren’t sacrificed on the altar of simplicity and convenience.
As the crypto landscape continues to evolve, it’s essential for industry leaders and developers to strike a harmonious balance between making technologies user-friendly and maintaining the rigorous security standards essential for protecting user assets and trust.
In a landscape as dynamic and rapidly evolving as cryptocurrency, discussions surrounding advancements and their accompanying challenges are not just inevitable but necessary. As users and stakeholders in this ecosystem, it’s crucial to stay informed, weigh the pros and cons, and make discerning choices that align with individual needs and the foundational principles of decentralized technologies.
For more detailed insights on this topic and ongoing discussions, stay connected with relevant contributors and keep abreast with the evolving trends and updates within the crypto world.
Remember, the journey of cryptocurrency is as much about innovation and adoption as it is about learning and making informed decisions every step of the way.
Continue reading
Continue reading

Ledger’s New Hardware Wallet Recovery Update: A Step Forward or A New Vulnerability?
May 16, 2023

Ledger’s New Hardware Wallet Recovery Update: A Step Forward or A New Vulnerability?
May 16, 2023