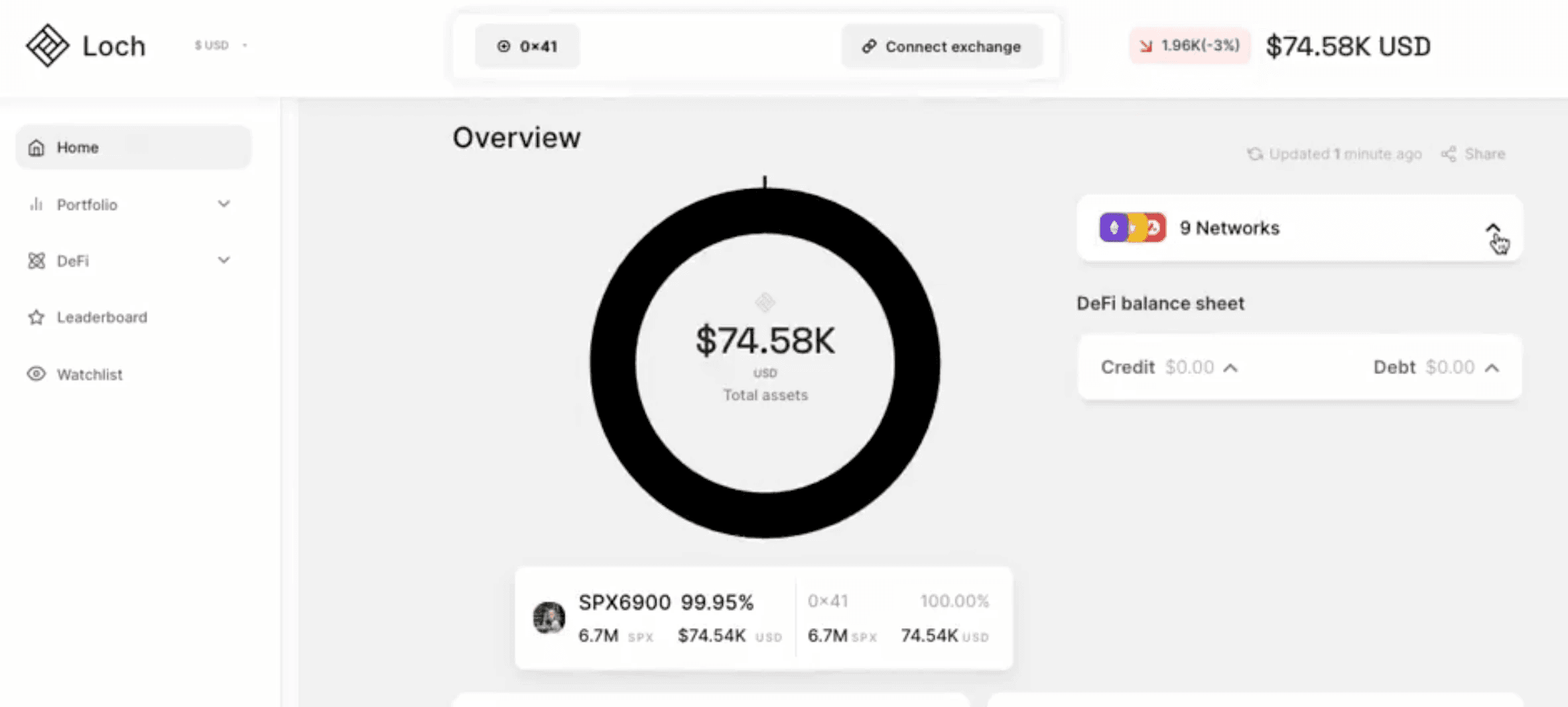
Key Insights from @VitalikButerin on Crypto & AI Applications
Vitalik Buterin's recent essay delves into the intricate connections and challenges posed by the integration of crypto and AI applications. Here are the key takeaways:
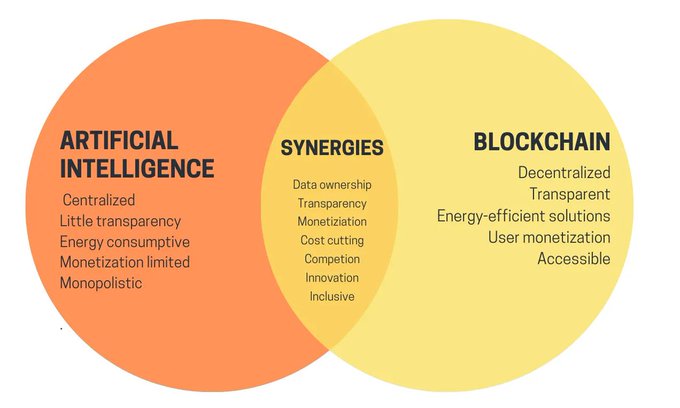
Superficial and Deep Connections:
While there are superficial connections between crypto and AI, such as decentralization and data storage, the deeper applications are less obvious. Recent advancements in Large Language Models (LLMs) and cryptographic tools have opened up new possibilities.
Potential Intersections Categorized:
The essay identifies four major areas where crypto and AI intersect:
1. AI as a Player in a Game Highest Viability:
- AIs participating in mechanisms with incentives sourced from protocols with human inputs.
- Examples include AI arbitrage bots in decentralized exchanges and prediction markets.
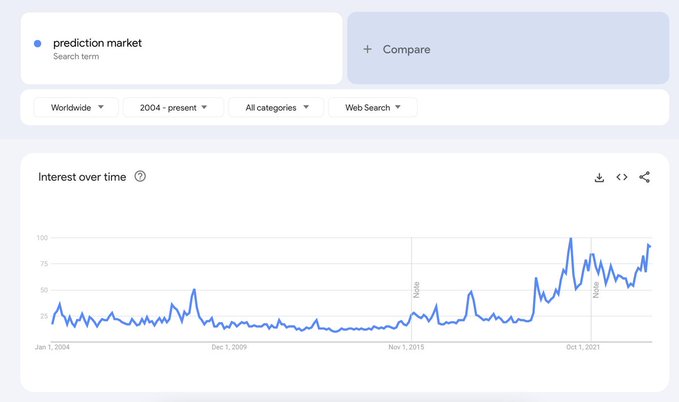
- Introduction of AIOmen, a prediction market with AIs as players, demonstrates potential.
2. AI as an Interface to the Game High Potential, with Risks:
- AIs aiding users in navigating the crypto world, offering explanations and preventing scams.
- Risks associated with adversarial machine learning attacks exploiting AI vulnerabilities.
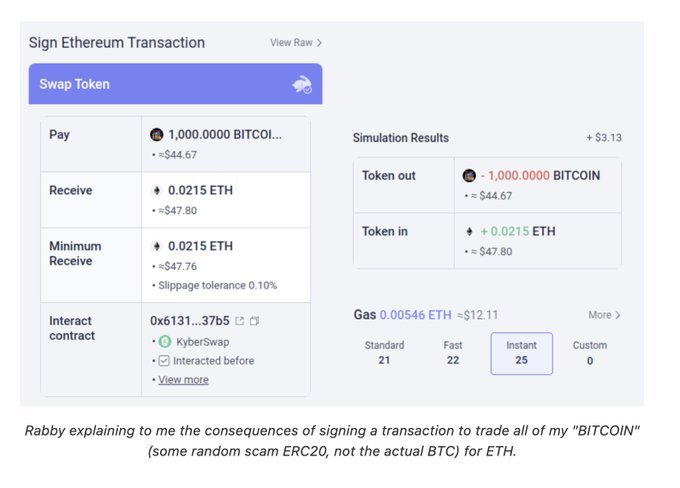
- Examples like Metamask's scam detection feature showcase AI-enhanced user protection.
3. AI as the Rules of the Game Tread Very Carefully:
- Integration of AI into decision-making processes like DAOs or smart contracts.
- Caution urged due to risks of adversarial machine learning and challenges in implementation.
4. AI as the Objective of the Game Longer-Term but Intriguing:
- Designing blockchains to construct and maintain AIs, focusing on incentivizing training and data misuse prevention.
- Potential applications in AI safety and decentralized governance.
Technical Challenges:
- Computational overhead of cryptographic methods and susceptibility of AI to black-box adversarial attacks.
- While computational intensity poses challenges, optimizations are possible in cryptographic contexts.
- Use cases where individual players become AIs, maintaining the underlying mechanism, are promising and easier to implement.
- Challenges arise in applications aiming to create a "singleton": a single decentralized trusted AI that applications rely on for specific purposes.
Vitalik Buterin's essay underscores the nuanced relationship between crypto and AI, highlighting potential avenues for innovation and cautionary considerations in their integration.
As the realms of crypto and artificial intelligence (AI) continue to evolve, Vitalik Buterin explores the intersections between these two significant technological trends. Acknowledging the collaborative efforts with teams like Worldcoin and Modulus Labs, as well as insights from individuals like Xinyuan Sun, Martin Koeppelmann, and Illia Polosukhin, Buterin delves into the promise and challenges of integrating crypto and AI.
The Quest for Synergy: Initial Perceptions and Evolution
People have long sought connections between crypto and AI, given their dominance in deep software technologies over the past decade. The superficial synergies, such as decentralization balancing AI centralization and blockchain addressing data needs, are apparent. However, specific applications have been less evident. In recent years, the landscape has transformed with the emergence of powerful AI models and cryptographic tools like Zero-Knowledge Proofs (ZKPs), Fully Homomorphic Encryption (FHE), and Multi-Party Computation (MPC).
Technical Challenges: A Balancing Act
In the intricate landscape where artificial intelligence (AI) and cryptography converge, Vitalik Buterin underscores the significance of navigating technical challenges. The interplay between these two complex domains requires a delicate balance to harness their full potential. Buterin sheds light on three key technical challenges:
1. Computational Overhead of Cryptographic Methods:
- The cryptographic methods employed to secure AI models can introduce computational overhead, posing a potential hurdle to efficient operations.
- Cryptography involves intricate algorithms for securing information, and the computational cost of these processes can be substantial.
- Balancing the need for robust security with the demand for computational efficiency is crucial, especially considering the inherently intensive nature of AI computations.
2. Susceptibility of AI to Black-Box Adversarial Attacks:
- Adversarial attacks are a persistent concern in the AI domain, and the challenge is heightened when AI models operate as "black boxes."
- A black-box AI refers to a system where the internal workings of the model are not transparent or easily interpretable.
- Buterin highlights the susceptibility of such AI models to adversarial attacks, where malicious actors exploit vulnerabilities without full knowledge of the model's internal mechanisms.
- These attacks can compromise the integrity of AI-driven systems, emphasizing the need for robust defense mechanisms.
3. Optimizations in Cryptographic Contexts:
- Despite the computational challenges posed by cryptographic methods, Buterin suggests that optimizations within cryptographic contexts can provide solutions.
- Cryptographic techniques, such as Zero-Knowledge Proofs (ZKPs) and Multi-Party Computation (MPC), offer avenues for enhancing the efficiency of AI operations within secured frameworks.
- The focus is on refining cryptographic protocols to minimize overhead while maintaining the integrity and privacy of AI computations.
- By optimizing the integration of cryptographic tools with AI processes, it becomes possible to strike a balance between security and computational efficiency.
Navigating the Future: Striking a Harmonious Balance
In essence, the technical challenges outlined by Buterin highlight the intricate dance between the computational demands of cryptography and the vulnerabilities inherent in AI systems. Striking a harmonious balance involves continuous research and innovation in cryptographic protocols, aiming to reduce computational overhead without compromising the security of AI models. The evolution of these technologies will likely see advancements that enable a seamless integration of AI and cryptography, unlocking new possibilities while safeguarding against adversarial threats. As the landscape matures, finding the optimal equilibrium between security and efficiency will be paramount for realizing the full potential of crypto + AI applications.
In conclusion, Buterin emphasizes the immediate promise and ease of implementation in use cases where existing mechanisms incorporate AIs as individual players. However, caution is urged in applications seeking to create a "singleton"—a single decentralized trusted AI—with potential high-value and high-risk implications. The evolving landscape of crypto + AI interactions invites exploration, experimentation, and careful consideration to unlock their full potential at scale. As both technologies advance, the synergies between crypto and AI are becoming more tangible, promising exciting developments in the future.
Disclaimer: This article is for informational purposes only and should not be considered financial advice. The mentioned projects may involve risks, and readers should conduct their research before making any investment decisions. The authors and the publication do not hold any responsibility for financial losses resulting from actions based on the information provided.
Via https://twitter.com/Prithvir12/status/1752300969323643169
Key Insights from @VitalikButerin on Crypto & AI Applications
Vitalik Buterin's recent essay delves into the intricate connections and challenges posed by the integration of crypto and AI applications. Here are the key takeaways:
Superficial and Deep Connections:
While there are superficial connections between crypto and AI, such as decentralization and data storage, the deeper applications are less obvious. Recent advancements in Large Language Models (LLMs) and cryptographic tools have opened up new possibilities.
Potential Intersections Categorized:
The essay identifies four major areas where crypto and AI intersect:
1. AI as a Player in a Game Highest Viability:
- AIs participating in mechanisms with incentives sourced from protocols with human inputs.
- Examples include AI arbitrage bots in decentralized exchanges and prediction markets.
- Introduction of AIOmen, a prediction market with AIs as players, demonstrates potential.
2. AI as an Interface to the Game High Potential, with Risks:
- AIs aiding users in navigating the crypto world, offering explanations and preventing scams.
- Risks associated with adversarial machine learning attacks exploiting AI vulnerabilities.
- Examples like Metamask's scam detection feature showcase AI-enhanced user protection.
3. AI as the Rules of the Game Tread Very Carefully:
- Integration of AI into decision-making processes like DAOs or smart contracts.
- Caution urged due to risks of adversarial machine learning and challenges in implementation.
4. AI as the Objective of the Game Longer-Term but Intriguing:
- Designing blockchains to construct and maintain AIs, focusing on incentivizing training and data misuse prevention.
- Potential applications in AI safety and decentralized governance.
Technical Challenges:
- Computational overhead of cryptographic methods and susceptibility of AI to black-box adversarial attacks.
- While computational intensity poses challenges, optimizations are possible in cryptographic contexts.
- Use cases where individual players become AIs, maintaining the underlying mechanism, are promising and easier to implement.
- Challenges arise in applications aiming to create a "singleton": a single decentralized trusted AI that applications rely on for specific purposes.
Vitalik Buterin's essay underscores the nuanced relationship between crypto and AI, highlighting potential avenues for innovation and cautionary considerations in their integration.
As the realms of crypto and artificial intelligence (AI) continue to evolve, Vitalik Buterin explores the intersections between these two significant technological trends. Acknowledging the collaborative efforts with teams like Worldcoin and Modulus Labs, as well as insights from individuals like Xinyuan Sun, Martin Koeppelmann, and Illia Polosukhin, Buterin delves into the promise and challenges of integrating crypto and AI.
The Quest for Synergy: Initial Perceptions and Evolution
People have long sought connections between crypto and AI, given their dominance in deep software technologies over the past decade. The superficial synergies, such as decentralization balancing AI centralization and blockchain addressing data needs, are apparent. However, specific applications have been less evident. In recent years, the landscape has transformed with the emergence of powerful AI models and cryptographic tools like Zero-Knowledge Proofs (ZKPs), Fully Homomorphic Encryption (FHE), and Multi-Party Computation (MPC).
Technical Challenges: A Balancing Act
In the intricate landscape where artificial intelligence (AI) and cryptography converge, Vitalik Buterin underscores the significance of navigating technical challenges. The interplay between these two complex domains requires a delicate balance to harness their full potential. Buterin sheds light on three key technical challenges:
1. Computational Overhead of Cryptographic Methods:
- The cryptographic methods employed to secure AI models can introduce computational overhead, posing a potential hurdle to efficient operations.
- Cryptography involves intricate algorithms for securing information, and the computational cost of these processes can be substantial.
- Balancing the need for robust security with the demand for computational efficiency is crucial, especially considering the inherently intensive nature of AI computations.
2. Susceptibility of AI to Black-Box Adversarial Attacks:
- Adversarial attacks are a persistent concern in the AI domain, and the challenge is heightened when AI models operate as "black boxes."
- A black-box AI refers to a system where the internal workings of the model are not transparent or easily interpretable.
- Buterin highlights the susceptibility of such AI models to adversarial attacks, where malicious actors exploit vulnerabilities without full knowledge of the model's internal mechanisms.
- These attacks can compromise the integrity of AI-driven systems, emphasizing the need for robust defense mechanisms.
3. Optimizations in Cryptographic Contexts:
- Despite the computational challenges posed by cryptographic methods, Buterin suggests that optimizations within cryptographic contexts can provide solutions.
- Cryptographic techniques, such as Zero-Knowledge Proofs (ZKPs) and Multi-Party Computation (MPC), offer avenues for enhancing the efficiency of AI operations within secured frameworks.
- The focus is on refining cryptographic protocols to minimize overhead while maintaining the integrity and privacy of AI computations.
- By optimizing the integration of cryptographic tools with AI processes, it becomes possible to strike a balance between security and computational efficiency.
Navigating the Future: Striking a Harmonious Balance
In essence, the technical challenges outlined by Buterin highlight the intricate dance between the computational demands of cryptography and the vulnerabilities inherent in AI systems. Striking a harmonious balance involves continuous research and innovation in cryptographic protocols, aiming to reduce computational overhead without compromising the security of AI models. The evolution of these technologies will likely see advancements that enable a seamless integration of AI and cryptography, unlocking new possibilities while safeguarding against adversarial threats. As the landscape matures, finding the optimal equilibrium between security and efficiency will be paramount for realizing the full potential of crypto + AI applications.
In conclusion, Buterin emphasizes the immediate promise and ease of implementation in use cases where existing mechanisms incorporate AIs as individual players. However, caution is urged in applications seeking to create a "singleton"—a single decentralized trusted AI—with potential high-value and high-risk implications. The evolving landscape of crypto + AI interactions invites exploration, experimentation, and careful consideration to unlock their full potential at scale. As both technologies advance, the synergies between crypto and AI are becoming more tangible, promising exciting developments in the future.
Disclaimer: This article is for informational purposes only and should not be considered financial advice. The mentioned projects may involve risks, and readers should conduct their research before making any investment decisions. The authors and the publication do not hold any responsibility for financial losses resulting from actions based on the information provided.
Via https://twitter.com/Prithvir12/status/1752300969323643169
Continue reading
Continue reading
Key Insights from @VitalikButerin on Crypto & AI Applications
Feb 4, 2024

Key Insights from @VitalikButerin on Crypto & AI Applications
Feb 4, 2024